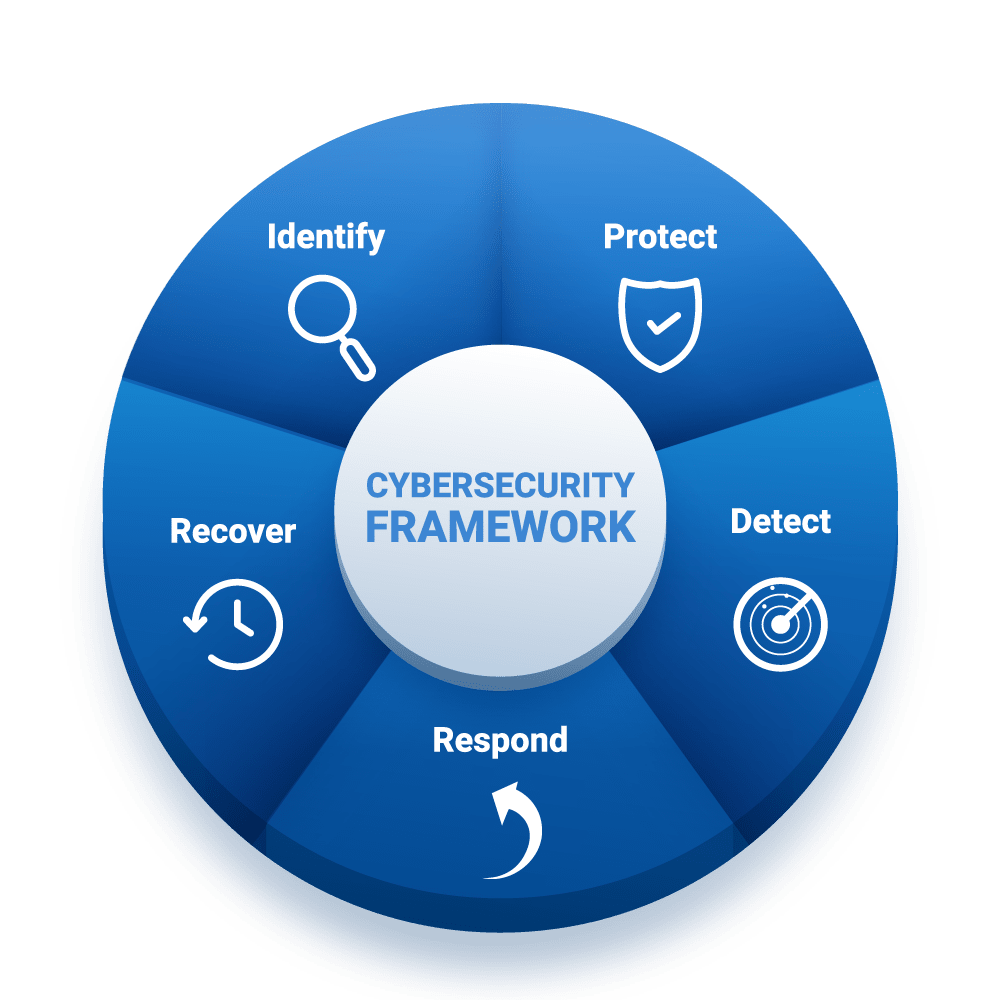
Cybersecurity Consulting Services
Empowering Businesses with Accessible Cybersecurity Solutions
At Core Insight, LLC, we believe that every business, regardless of size, should have access to top-tier cybersecurity services. Our approach is grounded in the following principles:
1. Structured Cybersecurity Services Without Cost Barriers: We provide a comprehensive cybersecurity framework that fits any budget, ensuring that financial constraints do not prevent businesses from achieving robust security.
2. Agile Security Programs: Our security solutions are designed to be flexible and adaptive, allowing your security program to pivot and meet evolving market demands and emerging threats. We ensure your business stays ahead of the curve in an ever-changing cybersecurity landscape.
3. Access to Skilled and Certified Partners: We connect you with experienced, certified cybersecurity professionals who are dedicated to guiding your business through current challenges and future growth opportunities. Our team works closely with you to align security strategies with your business goals.
Our scalable IT security consulting service streamlines the process of securing your business by reducing the time and resources spent on evaluating individual products and team members. With Core Insight, LLC, you get a trusted partner who simplifies cybersecurity, allowing you to focus on what matters most—growing your business.

What We Offer
Customized, No-Compromise Security Solutions
We provide a no-compromise security solution tailored specifically to your organization’s environment. By working closely with your management team, we ensure that your security policies and practices are perfectly aligned with your core business objectives, enabling you to advance your operational goals while maintaining robust security.
Our expertise spans multiple industries, allowing us to deliver solutions that meet the unique regulatory and compliance requirements of each sector:
- Government (GOV): Serving DoD, DHS, NIH with compliance to NIST Cybersecurity Framework (CSF)
- Healthcare: Ensuring HIPAA compliance to protect sensitive patient data
- Finance: Supporting SOX compliance to safeguard financial information
- Sports and Entertainment: Protecting digital assets and sensitive data
- Retail: Securing point-of-sale (POS) systems and ensuring PCI DSS compliance
- IT Support Services: Providing tailored security solutions to protect your IT infrastructure
Our industry-specific solutions are designed to help you achieve your security and compliance goals, protect critical assets, and enhance operational efficiency.
Fractional CISO - Service
Our Fractional CISO Service provides comprehensive oversight of your network and security operations, allowing your team to focus on core business initiatives. With our experienced vCISOs, you benefit from professionals holding industry-leading, vendor-neutral certifications, including CISSP, CISA, and CDPSE, ensuring your organization’s security is in expert hands.
Security Services
We offer a robust security service that seamlessly integrateswith your existing solutions. Our consultants hold certifications from leading vendors such as Microsoft, AWS, Splunk, and Cisco.
Additionally, our team includes experts with vendor-neutral certifications like CISSP, CISA, CDPSE, Security+, A+, and Network+, ensuring we provide the highest standard of security expertise.
Security Solutions
Protecting Your Most Important Assets: Data and Employees
We provide a range of solutions to safeguard your critical assets, including your data and employees:
- Backup and Recovery Planning, Testing, and Implementation: Ensure business continuity with a reliable backup and recovery strategy.
- Vulnerability Scanning, Reporting, and Remediation (NESSUS): Identify and address vulnerabilities to strengthen your security posture.
- Security Information and Event Management (SIEM) with SPLUNK: Gain visibility and insights into security events across your organization.
- Data Loss Prevention (DLP) Evaluation and Recommendations: Protect sensitive data with tailored DLP strategies.
- Identity and Access Management: Secure your organization by managing and controlling user access.
Our Approach to Security
Security Audits
Comprehensive Security Audits and Advisory Services
Our security audits ensure that your business has robust security policies in place to address all potential risks. We provide expert guidance on what assets to protect, how to protect them, and how to monitor and report data access, prioritizing the integrity of your data above all else.
We adhere to the NIST Cybersecurity Framework to provide a comprehensive approach to managing and reducing cybersecurity risks.
For our government customers, we also comply with NIST 800-53, NIST 800-171 (CMMC), JSIG, and the Risk Management Framework (RMF) standards.
Vulnerability Assessments
Identify and Mitigate Vulnerabilities in Your Information Systems
Let us help you uncover and mitigate vulnerabilities within your information systems. Our comprehensive process includes:
- Asset Discovery: Identifying all assets within your network.
- Asset Prioritization: Using a vulnerability scorecard to prioritize assets based on their criticality.
- Full Vulnerability Scanning: Conducting thorough scans to detect potential security weaknesses.
- Detailed Reporting: Providing in-depth reports on scan results.
- Targeted Remediation: Addressing and resolving vulnerabilities as needed to strengthen your security posture.
Security Analysis
Safeguard Your Assets Against Cyber Attacks
We help you identify, manage, and protect assets that may be vulnerable to cyber attacks. Our comprehensive security analysis involves a detailed assessment of your organization's digital infrastructure to uncover potential threats and vulnerabilities. We then provide actionable recommendations to mitigate these risks, ensuring your assets are secure.
By proactively addressing security weaknesses, we help safeguard your company's reputation and maintain the trust of your customers and partners. Our approach not only reduces the risk of breaches but also ensures compliance with industry standards and best practices, protecting your business from both financial loss and damage to your brand's goodwill.