Cyber Security Consulting Services
At Core Insight LLC. we operate with the mindset that all businesses, large or small, should have access to the following:
1. A structured cybersecurity service without cost restrictions
2. A security program that’s able to pivot to meet and exceed current market demands
3. Clients should have access to skilled and certified partners to help guide their current and future business decisions.
Our scalable IT security consulting service reduces the time and money spent on gathering and vetting individual products and team members.

What We Offer
We offer a no-compromise solution tailored to your environment. We work side by side with your management team to best align security policies and practices with your core business objectives in order to advance your operational goals.
We offer solutions within the following industries:
- GOV – DoD, DHS, NIH – NIST CSF
- Healthcare – HIPAA
- Finance – SOX
- Sports and Entertainment
- Retail – POS – PCI DSS
- IT Support Services
VCISOaaS - CISO as a Service
Our Virtual Chief Information Security Officer as a Service offering allows us to oversee the day to day management of your network and security operations, so your team can focus on other business initiatives. Our CISO’s have industry leading-vendor neutral certifications such as CISSP, CISA and CDPSE to name a few.
Security Services
We provide a robust security service that works with your current solution.
Our consultants posses certifications from vendors such Microsoft, AWS, Splunk and Cisco.
We also have staff with vendor neutral certificates such as CISSP, CISA, CDPSE, Security+, A+ and Network+
Security Solutions
We offer the following solutions to protect your most important assets, your data and employees.
- Backup and Recovery Planning, Testing and Implementation
- Vulnerability scanning, reporting and remediation – NESSUS
- Security Information and Event Management (SIEM) – SPLUNK
- Data Loss Prevention (DLP) evaluation and recommendations
- Identity and Access Management (IAM) – Active Directory, CyberArk, Xceedium
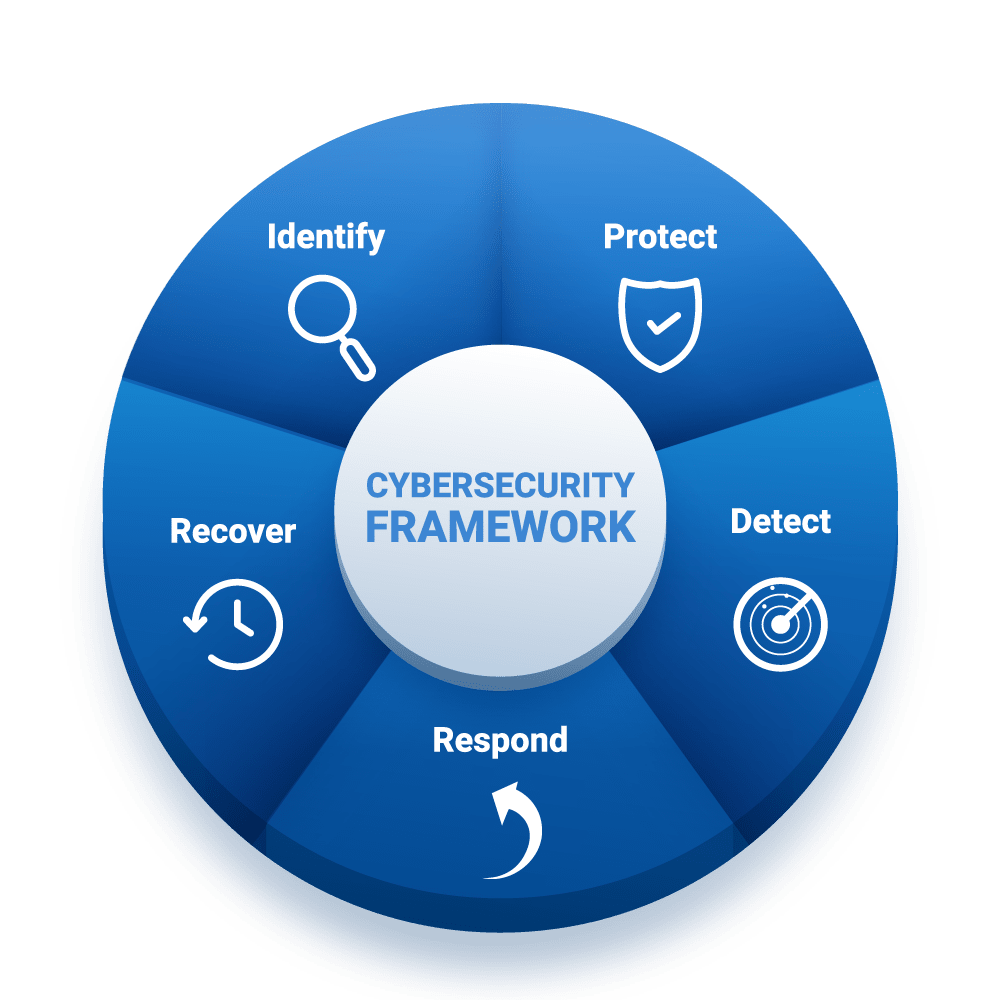
Our Approach to Security
Security Audits
Our security audits check and verify that your business has sufficient security policies in place to address all possible risks. We help advise on what to protect, how to protect it and how data access should be monitored and reported. The integrity of your data is of our upmost importance.
We follow the NIST Cybersecurity Framework.
For our GOV customers we adhere to the NIST 800-53, 800-171 (CMMC), JSIG and RMF
Vulnerability Prevention
Let us help identify and mitigate any vulnerabilities that exist within your information systems. Our process includes the discovery of all assets, prioritize asset using a vulnerability scorecard, perform a full scan, report on those results and remediate as appropriate.
Security Analysis
We help identify, manage and safeguard your assets that are vulnerable to a cyber attack. Our security analysis saves your company's reputation and good will.